AI for RFP Responses In 2026 (Detailed)
AI for RFP Responses In 2026 (Detailed)
Litigation doesn’t move quickly. After the initial filings, cases shift into discovery, and that phase can stretch for months or longer.
In a civil case, for example, once the complaint and response are filed, both sides begin exchanging documents and evidence. A significant amount of that time often goes toward responding to requests for production (RFPs).
No matter the practice area, drafting RFP responses requires careful review and precise wording. You analyze each request, collect documents, apply objections, and format everything correctly. The process is repetitive, but the consequences of sloppy language can be serious.
Artificial intelligence is beginning to reshape that workflow. RFP AI tools can organize prior language, draft structured responses, and reduce the time spent on mechanical edits. Some of the top AI tools focus on document-heavy legal works to help attorneys handle volume efficiently.
In this guide, we’ll look at how to use artificial intelligence in a practical way so it supports your discovery process and helps you manage RFP responses more efficiently.
What Are RFP Responses?
In litigation, RFP responses are your written answers to a request for production.
During discovery, the opposing side sends a list of documents and materials they want you to produce. You respond to each request, stating what will be produced and what objections apply.
A typical set of RFPs can get detailed fast. In a breach of contract case, for example, the other side might request “all communications between the plaintiff and any third party concerning performance of the agreement from January 1, 2022, to present.”
That one request can trigger a search through email accounts, shared drives, chat messages, and archived files.
Your response would clarify what documents are being produced, note any objections to scope or relevance, and state if anything is being withheld. Each answer becomes part of the formal discovery record.
This stage is a critical step in the RFP process. The way you answer questions can narrow disputes or create new ones. So, clear, precise responses help move the discovery process forward and reduce the chances of follow-up fights.
How Does AI Make a Difference?
Drafting RFP responses takes time. Usually, you’re reviewing requests, pulling documents, checking prior language, and making sure every objection and production statement lines up.
AI can help you work through that load in a more structured way. Used correctly, it supports your process without taking control of it.
Here’s where it makes a difference:
- Faster first drafts: AI RFP response software can generate structured responses based on prior filings or templates, which gives you a solid starting point.
- More accurate answers: When trained on your approved language and past responses, AI helps maintain consistency in objections, definitions, and formatting.
- Reduced repetitive drafting: Standard objections and common response language don’t need to be rewritten from scratch every time.
- Higher quality responses: With less time spent on formatting and repetition, you can focus on strategy, clarity, and case-specific nuance.
Take note that AI won’t replace judgment. You still review every response. What it can do is remove some of the mechanical drafting work to give you space to think through the bigger discovery strategy.
Should You Use AI to Respond to RFPs?
You’ve seen how AI can save time. The better question is whether it makes sense for your legal workflow.
If your team handles a steady stream of requests for production, you are likely familiar with how repetitive parts of the process can feel. RFP response automation can handle much of that routine drafting.
There’s also the accuracy piece. AI can help catch errors like inconsistent terminology or missing response language, especially when it’s trained on your prior filings.
Still, not every matter is a good fit. Complex cases with unusual legal issues or sensitive facts demand close attention from start to finish. With that in mind, AI should support your drafting, but not make judgment calls.
For most companies and law firms managing ongoing discovery, the practical benefit is efficiency. You reduce manual work tied to repetitive tasks and gain time to focus on strategy.
Step-by-Step: How to Use AI for RFP Responses
Once you decide AI has a place in your discovery workflow, the next step is using it in a way that supports your existing process.
Here’s a simple step-by-step guide to give you something to base your process on:
1. Build a Structured Response Library
AI can only draft from what you give it. Before you plug anything into an AI platform or RFP software, organize your past responses into a clean, reliable content library.
Start by collecting prior RFP responses, standard objections, recurring definitions, and any formatting your team consistently uses. Then, review everything carefully. Remove outdated language and align terminology. Make sure the material reflects how you currently approach discovery.
Approved content libraries are what make accurate responses possible. If the source material is inconsistent, the output will be too.
This is also where customized prompts come into play. Once your content is organized, you can guide the system to draft in a way that matches your tone and structure.
When set up properly, AI works as a writing partner that builds from language you’ve already vetted rather than guessing at what you meant.
You might want to include:
- Standard discovery objections
- Definitions and general instructions
- Common response language
- Formatting templates
- Prior court-approved responses
- Case-specific variations
2. Select an AI RFP Response Tool
Once your content library is organized, the next step is choosing the right RFP tool.
Not all AI RFP software is built the same, especially in a legal discovery context. You want technology that supports structured drafting, consistent objections, and production-ready formatting.
Look for robust features like document parsing, objection-aware drafting, Word export, and secure data handling. Strong RFP automation should reduce manual formatting and repetitive drafting without taking control away from you.
Briefpoint is one example built specifically for legal discovery. It allows you to propound and respond to requests for production, interrogatories, and requests for admission. Plus, its Autodoc feature can turn large productions into Bates-cited, formatted responses in minutes.
Firms use it to cut response time dramatically while keeping review and verification in their hands. It’s SOC-2 certified, works in all 50 states and federal courts, and doesn’t use your data to train outside models.
When evaluating any AI RFP software, focus on security, accuracy, and how well it fits your existing workflow.
If you want to see how Briefpoint handles RFP automation in practice, book a demo here.
3. Upload and Organize Prior Responses
After choosing your tool, start feeding it the material you already rely on. Upload prior RFP responses, standard objections, formatting templates, and definitions so the system can begin leveraging AI with trusted language.
Good knowledge management makes a real difference here. If your files are scattered or inconsistently labeled, your RFP workflows will feel the same way.
Also, group responses by case type, subject matter, or request category. Keep recurring objections in one place. Separate general instructions from case-specific language.
For example, if you regularly handle personal injury cases, create a section for common medical record objections, time-frame limitations, and ESI language used in those matters. When a similar request comes in, the tool can pull relevant content without digging through unrelated files.
4. Analyze Incoming Requests for Production
Before drafting anything, take time to review the incoming RFP carefully. AI can help by summarizing long sets of RFP questions and highlighting key themes, time frames, and definitions.
Start by identifying what’s actually being asked. Are the requests broad? Do they overlap? Are certain terms undefined or ambiguous? A quick AI-assisted summary can surface patterns that aren’t obvious at first glance.
You can also compare the new requests against past proposals or prior RFP responses in similar cases. That side-by-side review helps you see where standard language applies and where the facts require something more tailored.
For instance, if multiple requests target communications during a specific date range, grouping them early makes collection and drafting more efficient.
5. Generate Initial Draft Responses
Now you’re ready to draft, and this is where generative AI can save serious time. Rather than typing out each response manually, you prompt the system with the specific RFP questions and relevant case details.
Always remember that clear instructions make a difference. If you include the date range, defined terms, and any known objections, most AI models can assemble a solid first draft using your approved language.
You can use it to generate:
- Tailored objections that track the wording of the request
- Production statements in your firm’s standard format
- Definitions and general instructions
- Discovery responses that pull from similar past matters
This draft won’t be the final version, and it shouldn’t be. Human input is still critical. You’ll review for accuracy, confirm the facts, and adjust tone based on your strategy. This brings us to the next step.
6. Review and Refine For Case Strategy
Now you read the draft like opposing counsel would. AI-native platforms can assemble responses quickly, but they don’t understand your litigation posture or the nuances of your client’s facts.
Start with a manual review. Confirm that each objection matches your intended position. Check that production language reflects what you’re actually prepared to turn over. Look closely at defined terms and time frames.
Bring in subject matter experts if the requests touch technical systems, medical records, financial data, or retention policies. That input can prevent overbroad statements or factual mistakes.
As you refine, ask:
- Does this response align with our overall discovery strategy?
- Are we preserving arguments for later motions?
- Is any language broader than necessary?
- Could this answer create avoidable disputes?
- Does the tone reflect how we want to approach opposing counsel?
7. Conduct Final Accuracy and Compliance Check
Before serving your responses, take one last pass focused purely on accuracy and compliance. Even strong AI-generated content can contain small inconsistencies or assumptions that need correction.
This review is less about style and more about protecting your client and your record.
It typically includes:
- Fact verification: Confirm names, dates, defined terms, and references match the case file and the specific client’s information.
- Production alignment: Double-check that every production statement reflects what is actually being produced and nothing more.
- Objection consistency: Make sure objections are applied uniformly and don’t conflict with one another.
- Confidentiality review: Confirm that customer data, medical information, or sensitive business materials are properly designated and handled.
- Formatting and jurisdiction rules: Verify captions, numbering, and formatting comply with local court requirements.
This final step can also surface valuable insights about gaps in your process or language that need updating in your templates.
Proposal teams and litigation teams alike benefit from this kind of structured closeout. It’s the last safeguard before the responses leave your hands.
Best AI Tools for RFP Responses
There isn’t one single type of legal AI tool for RFP work. What makes sense for your team depends on how often you handle discovery, how complex your matters are, and how sensitive the data is.
Some tools you can choose from include, but are not limited to:
- Dedicated RFP automation software: These platforms focus on RFPs and security questionnaires. They usually include a searchable knowledge base, version control, collaboration tools, and intelligent automation that pulls approved language into structured drafts.
- Litigation-focused drafting platforms: These tools are designed specifically for legal discovery. They help draft and respond to RFPs, interrogatories, and RFAs using structured templates and objection-aware language.
- Enterprise knowledge management systems: Larger firms often use internal systems to store and organize past responses. These tools strengthen version control and make it easier for multiple contributors to work from the same approved content.
- General public AI models: Public AI models and other inventive AI tools can draft quickly, but they require close supervision when handling confidential material.
Manage More RFPs With Briefpoint
Responding to requests for production is detailed work. Every objection has to line up. Every production statement has to reflect what’s actually being turned over. Formatting, captions, Bates numbers, deadlines — none of it can be off.
Briefpoint was built with that reality in mind.

Discovery is a good example. It’s deadline-driven, detail-heavy, and often repeated across matters.
Briefpoint helps you propound and respond to RFPs, interrogatories, and RFAs in a structured, objection-aware format that reflects how discovery actually works.
With Autodoc, you can upload your complaint, the RFPs, and your production files, then generate formatted, Bates-cited responses in minutes. You still review everything, and you still control the strategy. The platform handles the heavy drafting and organization.
For firms that manage consistent discovery volume, those time savings can make a difference in your litigation process. It allows you to take on more RFPs without stretching your team or compromising quality, and that consistency becomes a clear competitive advantage over time.
FAQs About Using AI for RFP Responses
What is the 10-20-70 rule for AI?
The 10-20-70 rule is a simple way to think about how AI fits into professional work. Roughly 10% is the tool itself, 20% is how you configure and prompt it, and 70% is the human review and judgment that shapes the final result. In RFP drafting, AI can generate a structured starting point, but legal strategy, risk analysis, and final decisions still rely on you.
What is the AI tool to generate responses?
There isn’t one single tool. Some teams use dedicated RFP automation platforms with workflow automation and knowledge management features. Others rely on litigation-focused tools like Briefpoint. General AI systems can also draft responses, but they require careful review to avoid generic answers and confirm that the right answer is reflected.
Can AI provide instant answers to complex RFP questions?
AI can generate instant answers, but speed doesn’t guarantee accuracy. Complex legal issues, technical jargon, and case-specific facts still require attorney review to improve quality and prevent mistakes.
How does AI help teams stay organized during RFP workflows?
Many platforms include features to track progress, send real-time notifications, and maintain version control. Some tools even remember past edits and provide real-time feedback, which can create a competitive edge when managing multiple deadlines. Security documentation and a clear trust center are also important when handling sensitive client data.
The information provided on this website does not, and is not intended to, constitute legal advice; instead, all information, content, and materials available on this site are for general informational purposes only. Information on this website may not constitute the most up-to-date legal or other information.
This website contains links to other third-party websites. Such links are only for the convenience of the reader, user or browser. Readers of this website should contact their attorney to obtain advice with respect to any particular legal matter. No reader, user, or browser of this site should act or refrain from acting on the basis of information on this site without first seeking legal advice from counsel in the relevant jurisdiction. Only your individual attorney can provide assurances that the information contained herein – and your interpretation of it – is applicable or appropriate to your particular situation. Use of, and access to, this website or any of the links or resources contained within the site do not create an attorney-client relationship between the reader, user, or browser and website authors, contributors, contributing law firms, or committee members and their respective employers.
MyCase vs. PracticePanther: What Are the Key Differences?
MyCase vs. PracticePanther: What Are the Key Differences?
Picking the right practice management software can take more effort than most people expect. MyCase and PracticePanther both offer solid features, but the experience you get from each one feels different once you’re actually using them.
If you’ve been trying to figure out which one lines up with the way your firm operates, this comparison lays everything out in a clear, practical way.
You’ll see how each platform approaches daily tasks, where their strengths show up, and what kind of team each one tends to fit best.
What Is MyCase?
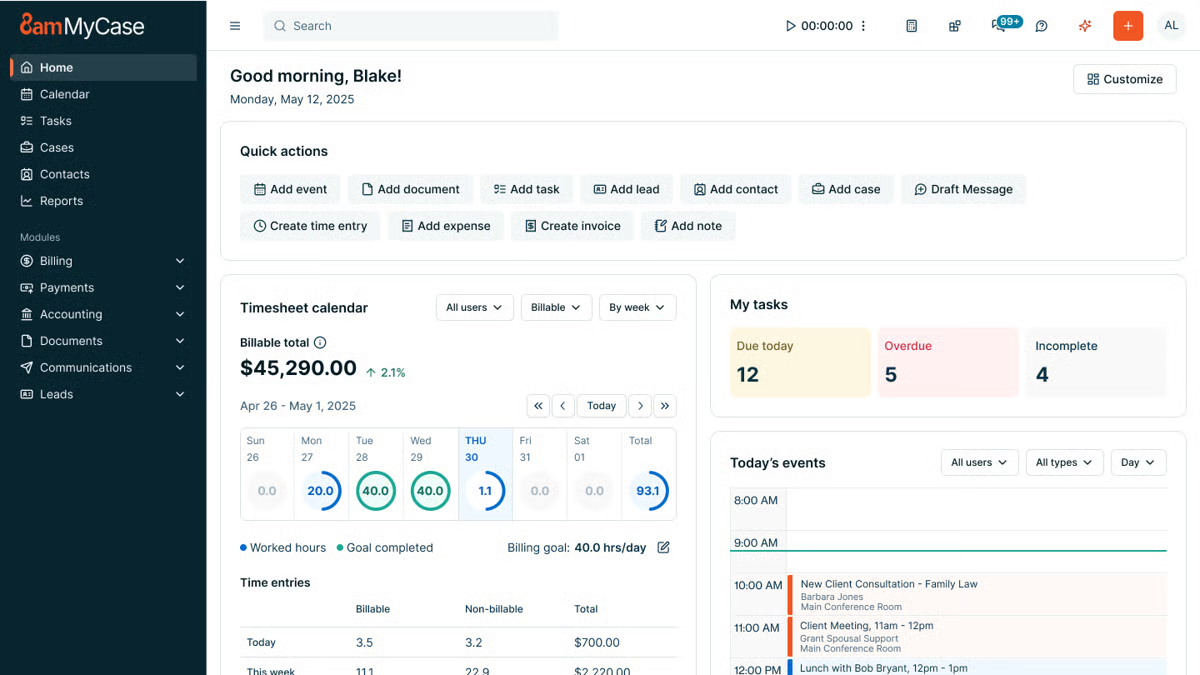
MyCase is a cloud-based legal practice management software that gives you one place to organize your firm’s work. It’s essentially a system that keeps your tasks, contacts, billing, calendar, and legal documents from living in ten different tabs.
It first launched in 2010 and quickly picked up traction with small and midsize firms that wanted something modern but easy to learn.
Source: G2
Part of its appeal comes from its straightforward layout. You don’t need a week of training to get comfortable. Most users jump in and start managing matters, sending invoices, or uploading documents without much friction.
Its document management setup is also a big reason people choose it. You can store files, share them with your team, and keep everything tied to the right case.
Something else you might appreciate is how client-friendly it feels. The built-in portal, online payments, and messaging tools help you cut down on emails and long phone chains. Clients get a clearer view of what’s happening, and you spend less time tracking small updates.
Overall, MyCase works well for firms that want an all-in-one platform that keeps everyday tasks moving and brings your documents, communication, and case details into one organized space.
What Is PracticePanther?
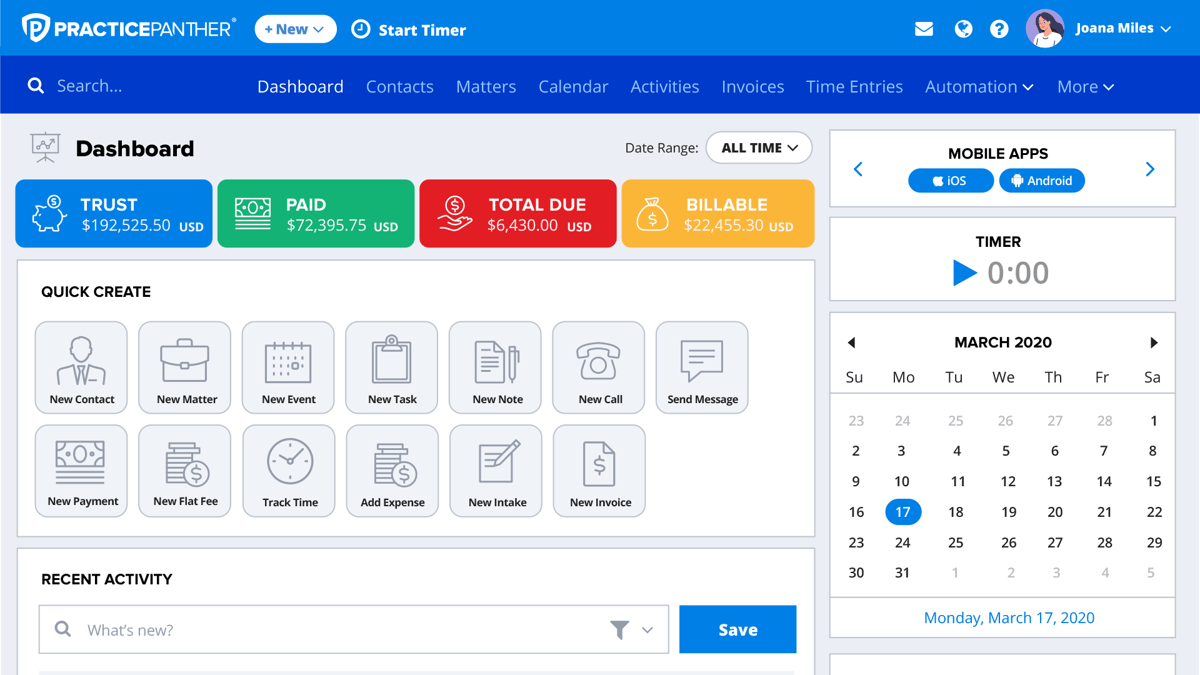
PracticePanther is a legal practice management platform built for firms that want a system they can grow into.
You get a cloud-based dashboard that brings your matters, billing, calendar, and communication together, but the real draw is how flexible the software feels once you start using it.
Source: G2
If you’ve ever felt boxed in by rigid legal workflows, this tool tends to be a nice change of pace. You can customize tasks, automate repetitive steps, and shape processes around the way your firm already works.
In other words, it’s designed to support everything from simple daily checklists to more specific tasks that vary from case to case.
Another standout trait is its connection to third-party tools and apps for lawyers. Email, payment processors, document services; PracticePanther plugs into many of the platforms firms already rely on, which keeps transitions smooth and avoids extra busywork.
And because the platform scales well, it fits solo attorneys just as comfortably as expanding teams. You get comprehensive features, plenty of control over how you work, and a structure that adapts as your caseload grows.
MyCase vs. PracticePanther: An In-Depth Comparison
Not sure which tool to choose? This quick comparison gives you a clearer sense of which option fits the way your firm actually works.
Main Purpose
When you look at the core purpose of each platform, the differences become easier to spot.
MyCase simplifies daily work for law firms that want an organized, all-in-one hub. Its goal is to cut back on time-consuming admin tasks and give you a straightforward system for matters, billing, communication, documents, and more.
If you want something that works smoothly as long as you have an internet connection and doesn’t overwhelm your team, MyCase offers a very direct path.
PracticePanther takes a slightly different angle. The platform aims to give firms more control over how they work, offering deeper customization and more flexible workflows.
PracticePanther excels when you want to tailor your processes, connect with third-party tools, and build out legal automations that match your firm’s habits. It also focuses on scalability, so teams with growing caseloads or more complex workflows often appreciate its structure.
When you’re comparing MyCase and PracticePanther, it really comes down to what you value most.
Overall, MyCase offers simplicity and a clean workflow that keeps everything in one place. PracticePanther offers more advanced functionality and the freedom to shape the software around your firm. Both solve everyday challenges, just in different ways.
Key Features
Taking a closer look at the features helps you understand how each platform supports your daily flow and where its strengths differ:
MyCase’s Key Features
- Secure client portal: Clients can view case files, send secure messages, and pay invoices while keeping everything confidential.
- Automated time tracking: Tracks time as you work, so billing and completing invoices feel easier.
- Customizable invoicing: Lets you adjust formats, payment options, and payment history.
- Document solution: Stores case files, supports customizable templates, and connects with Google Drive.
- Google Calendar sync: Keeps deadlines and events aligned across your devices.
- Accounting software: Helps you manage retainers and trust balances accurately.
- Client communications: Offers secure messages and organized updates in one place.
PracticePanther’s Key Features
- Custom fields and custom tags: Lets you tailor matters with details that match your legal workflow.
- Automated time tracking: Captures billable time in the background.
- Customizable templates: Helps you create repeatable documents for recurring or specific tasks.
- Third-party integrations: Works with Google Drive, payment systems, email tools, and other solutions.
- Secure client portal: Gives clients protected access to documents, invoices, and messages.
- Trust accounting: Tracks retainers, payments, and transfers with clear reporting.
- Reporting dashboard: Helps you gain insights into billing performance and law firm productivity.
Who It’s Best For
MyCase usually clicks with lawyers who want something they can get comfortable with right away. If your priority is a clean layout, easy case management, and quick access to the basics, it fits that style well.
Legal professionals who don’t want to spend time configuring every detail tend to appreciate how smoothly it handles law firm communication, scheduling, and billing. It’s especially appealing for small firms or teams that want things organized without juggling extra setup.
PracticePanther leans toward firms that like having more control. If your practice area involves complex steps, custom fields, or a need to connect with a bunch of other tools, the platform gives you that extra flexibility.
Many lawyers choose it because they want something that grows with their client base and adapts as workloads shift. Its advanced features and customization options make it a comfortable match for teams with expanding needs or more structured workflows.
Pricing
Pricing for both platforms depends on the plan you choose and the size of your team, but here’s what you can expect at a high level.
MyCase Pricing
- Basic plan: $49 monthly: Core case management, billing, payments, client messaging, and the secure client portal.
- Pro plan: $99 monthly: Everything in Basic plus advanced reporting and enhanced document management tools.
- Advanced plan: $119 monthly: Adds MyCase Drive, advanced document automation, and expanded analytics.
PracticePanther Pricing
- Solo plan: $59 monthly: Designed for individual attorneys with core case management, billing, and calendar tools.
- Essential plan: $79 monthly: Adds integrations, automated workflows, and more robust document management.
- Business plan: $99 monthly: Includes advanced features like deeper automation, advanced reporting, and more customization options.
Add Briefpoint to Strengthen Your Legal Tech Stack
Choosing between MyCase and PracticePanther comes down to what your firm values. Both tools cover case management, billing, communication, and client-facing features, so you’re already headed in the right direction with either one.
That said, no practice management platform handles everything on its own, especially when you’re dealing with heavy document work.
This is where Briefpoint becomes a smart addition to your legal tech stack. It automates routine litigation drafting, helps you move through legal documents faster, and keeps your work product consistent across matters.

If you’re already using systems like MyCase or PracticePanther, Briefpoint fits right in by handling the pieces those platforms don’t focus on.
You can also take advantage of the Autodoc feature for quick, accurate document assembly when you’re under pressure with multiple deadlines. It generates ready-to-serve discovery responses, complete with Bates numbering and page-level citations, so you’re not piecing things together manually.
The combination saves time and keeps your workflows running smoothly, no matter which practice management system your firm prefers.
FAQs About MyCase vs. PracticePanther
What is legal practice management software?
It’s a platform that helps law firms organize daily work (case details, calendars, billing, documents, and communication) so nothing slips through the cracks. A good system offers an intuitive interface, keeps data organized, and supports client confidentiality across various channels.
Is MyCase a good software?
Yes. Many firms like MyCase because it’s easy to learn, keeps case information in one place, and offers helpful tools for communication, billing, and document management. It’s designed for lawyers who want a simple setup with comprehensive support behind it.
How much does PracticePanther cost?
PracticePanther has three tiers: Solo, Essential, and Business. Pricing ranges from the mid-$40s to the high-$90s per user/month, depending on the plan and billing cycle. The higher tiers come with more advanced automation, reporting, and customization. This structure makes PracticePanther a scalable platform that firms can grow into.
What kind of software is MyCase?
MyCase is cloud-based legal practice management software. It helps you manage cases, communicate with clients, track time, send bills, and view invoices, all from one centralized dashboard.
What is the difference between Lawmatics and MyCase?
Lawmatics focuses on legal CRM, intake, and marketing automation, while MyCase centers on case management and day-to-day firm operations. Lawmatics helps firms attract and nurture leads, while MyCase supports ongoing case work and the tasks that come after a client signs on. PracticePanther stands as another case management option if you want more customization than MyCase but broader functionality than a CRM-focused tool.
The information provided on this website does not, and is not intended to, constitute legal advice; instead, all information, content, and materials available on this site are for general informational purposes only. Information on this website may not constitute the most up-to-date legal or other information.
This website contains links to other third-party websites. Such links are only for the convenience of the reader, user or browser. Readers of this website should contact their attorney to obtain advice with respect to any particular legal matter. No reader, user, or browser of this site should act or refrain from acting on the basis of information on this site without first seeking legal advice from counsel in the relevant jurisdiction. Only your individual attorney can provide assurances that the information contained herein – and your interpretation of it – is applicable or appropriate to your particular situation. Use of, and access to, this website or any of the links or resources contained within the site do not create an attorney-client relationship between the reader, user, or browser and website authors, contributors, contributing law firms, or committee members and their respective employers.
Early Case Assessment: eDiscovery Essentials
Early Case Assessment: eDiscovery Essentials
How do you get a clear picture of a case before the full weight of discovery hits your desk?
Early case assessment (ECA) is the step that gives you that clarity. It helps you understand the scope of the matter, the type of data involved, and the issues that may guide your next moves.
A quick early review makes it easier to plan resources, set expectations, and avoid surprises later.
With ECA, you’re looking at small samples, checking early patterns, and getting familiar with the information that supports smarter decisions. It creates a smoother path into the rest of the eDiscovery process because you already know what deserves attention and what can wait.
This guide walks through how ECA works, why it matters, and how the right tools can make those first stages more manageable and consistent.
What Is Early Case Assessment in eDiscovery?
Early case assessment gives you a faster read on the size and direction of a legal matter before the full discovery work begins. You’re taking an early look at potentially relevant data, spotting what’s clearly irrelevant, and getting a sense of the risks, timelines, and costs that might follow.
Law firms and legal teams use this step to avoid surprises and decide how much effort a case may require.
An early case assessment process usually includes gathering a sample of data, running quick searches, and reviewing patterns that hint at what the larger collection will look like.
That early snapshot sets the stage for smarter decisions, whether the goal is negotiating, narrowing the scope, or preparing for deeper review later.
The focus is basically on conducting a comprehensive evaluation before the heavy lifting starts. You get clarity on custodians, data sources, and core issues long before documents pile up.
Why Early Case Assessment Matters
Taking a moment to understand a legal case early helps you step into the rest of the litigation process with fewer surprises.
Legal professionals get a clearer read on how much data they’re facing, what looks useful, and which potential risks might shape strategy later. It sets a more grounded plan before the heavier review work begins.
Here’s how an early look makes a difference:
- Stronger clarity: You get a quick sense of the most relevant data and what can be set aside, which makes the next steps smoother.
- Better forecasting: Understanding how much data needs attention helps you plan timelines and set expectations without guessing.
- Smarter strategy: Early awareness of potential risks gives you room to adjust your approach before things get complicated.
- More focused review: Filtering out obvious irrelevant data at the start keeps the team focused on information that actually supports the legal matter.
- A more defensible approach: Consistent steps, documented searches, and early data analysis help build the most defensible process for the rest of the case.
This kind of early check-in gives you direction and confidence before review work grows in size or cost.
5 Key Components of an Effective ECA Process
A solid early case assessment works best when you break it into a few focused steps. Consider this section as a quick guide you can use to get a cleaner view of your case data before the eDiscovery process grows in size and cost.
1. Identifying Key Custodians and Data Sources
An effective assessment starts with knowing who holds the most critical information. This involves examining key custodians, where their electronically stored information (ESI) lives, and how much of it may matter to the case.
You might look at email accounts, shared drives, chat platforms, and even paper documents if they still play a role.
A few things to confirm early:
- Data locations that truly matter
- Any potential gaps based on job roles
- Sources that might contain relevant documents
Getting this right gives you a complete picture before search terms or a deeper review begins.
2. Collecting a Manageable Sample of Case Data
You don’t need a full collection at this stage; you only need enough to understand patterns.
A small sample of potentially relevant ESI can show you early themes, topics, and data volume without pulling in every file. Many teams use early case assessment software here to review samples quickly, highlight irrelevant data, and spot red flags.
This makes room for quicker, informed decisions before investing in a full review. It also creates an opportunity to confirm which data sources should be prioritized once production planning starts.
3. Conducting Custodian Interviews
Talking directly to the people involved gives you far more context than metadata alone. These conversations help you pinpoint critical information, understand communication habits, and confirm how the parties involved handled files, messages, or other materials.
During interviews, you might explore:
- How information was shared inside and outside the team
- Topics or terms that may guide searches later
- Any unique tools or storage locations that custodians rely on
These insights guide your next moves and reduce the chance of overlooking important sources.
4. Running Early Searches and Filtering
Once you understand where the information lives, quick searches help you narrow the scope. You’re looking for patterns that highlight what’s relevant, what can be pushed aside, and what may require detailed analysis later.
This step often uncovers communication threads, timelines, and early indicators of potential issues with opposing counsel.
A well-planned search also reduces unnecessary review work, which keeps the project lean while maintaining accuracy.
5. Using Reports and Data Visualization Tools
Clear visuals help you understand the story your data tells. Data visualization tools can show communication spikes, custodians with heavy activity, or time periods that warrant closer review.
These reports support informed decisions because you’re not relying solely on text or spreadsheets.
Charts, heat maps, and timelines often reveal patterns that are easy to miss in raw data. This can help you assess risks and decide how to move forward with confidence.
How eDiscovery Software Supports ECA
The right tools make early case assessment feel far more manageable. You’re taking large sets of raw data and turning them into something you can actually understand, which helps you build a clearer case strategy before review work grows.
Early case assessment tools often start by pulling in data from multiple sources, indexing it, and giving you an easy way to search across everything at once. That alone helps you spot crucial data early.
From there, features like filtering, analytics, and reporting help you narrow the focus so you’re not spending time on information that doesn’t support the matter.
Many platforms also offer quick ways to identify responsive documents, surface keywords and communication patterns, and get a sense of who’s involved in conversations that matter.
In other words, you’re basically getting a preview of the story your data tells before you commit to a full document review.
Common features that make this step easier include:
- Fast searching across raw data
- Visual summaries that show patterns or high-activity custodians
- Filtering tools that separate useful information from noise
- Early tagging to help teams stay aligned
All of this gives you the context you need to make smart choices early, reducing unnecessary work and pointing your team toward the areas that deserve attention first.
Benefits of Using ECA Tools
We talked earlier about the value of early case assessment, and the legal software side adds another layer of support.
These tools help you move through the early stages with more clarity, less manual effort, and a better understanding of where the case may be heading.
Here are the core benefits:
- Faster insight: ECA tools help you spot relevant information quickly so you’re not digging through large volumes of data to find what matters.
- Lower project costs: Early filtering and guided searches keep the focus on potentially responsive documents, which leads to meaningful cost savings later in the project.
- Clearer strategy development: Early visibility into key issues gives you what you need to shape a stronger litigation strategy without waiting for full review.
- More accurate conclusions: Better organization and early analysis give you a clearer read on the case, which helps you avoid missteps and premature assumptions.
- Stronger team alignment: Everyone works from the same information to make it easier to stay coordinated as the matter grows in size and complexity.
Early Case Assessment Checklist
A quick checklist gives you a simple way to stay organized as you work through the early steps of a matter. It keeps you focused on the essentials, helps you avoid missing potentially relevant information, and gives everyone involved a clearer view of the available data before deeper review begins.
Here are the core items worth confirming:
- Identify key legal issues and the people most connected to them
- Confirm what collected data you actually have and what’s still missing
- Check all likely locations for potentially relevant information
- Review a small sample to understand the tone, topics, and data review needs
- Talk with custodians to clarify context and storage habits
- Map out the entire dataset so risk managers understand the scope
- Estimate potential costs based on volume, timing, and complexity
- Use eDiscovery tools to organize early findings and highlight patterns
- Flag dates, keywords, and communication threads that need closer attention
- Document early insights so the rest of the matter stays consistent
How Briefpoint Supports Your Early Case Assessment Work
An early case assessment gives you a head start. You’ve already sorted through the noise, spotted key documents, and built a clearer view of the case before the heavy data review begins.
At this point, it’s all about turning those early insights into something you can use without spending significant time on tasks that slow everyone down.
This is where Briefpoint’s Autodoc fits in naturally. Once you understand your available data, Autodoc helps you move from early analysis to finished discovery responses without the usual page-turning.
You upload your files, and the tool finds responsive material, generates Bates-numbered outputs, and packages everything in a format you can serve with confidence. It takes the work that usually drags on for days and turns it into a cost-effective process that feels straightforward.
If you want to see how much time your team can save, you can book a demo and see Autodoc for yourself.
FAQs About Early Case Assessment in eDiscovery
What does ECA mean in eDiscovery?
It refers to taking an early look at potentially collectible ESI to understand the scope, key dates, and the overall direction of a matter before the detailed review work begins. This helps teams size the project, spot risks, and plan next steps with clarity.
What does early case assignment mean?
It’s the point when a new legal matter is handed off and the team begins gathering background details. You’re identifying the main issues, the people involved, and the information that deserves attention, so everything starts from the right foundation.
What is an ECA tool?
An ECA tool helps organize the first wave of information. It can pull data together, surface patterns, run quick searches, and highlight potentially relevant material. Some platforms also use data analytics or advanced analytics tools to give you a clearer view of communication trends or activity spikes.
What is the ESI discovery process?
It’s the workflow for handling electronically stored information. This includes finding data sources, confirming appropriate countries for collection, gathering what matters, and preparing files for the opposing party. A smooth process keeps everything consistent and allows legal teams to move from early assessment to production without confusion.
The information provided on this website does not, and is not intended to, constitute legal advice; instead, all information, content, and materials available on this site are for general informational purposes only. Information on this website may not constitute the most up-to-date legal or other information.
This website contains links to other third-party websites. Such links are only for the convenience of the reader, user or browser. Readers of this website should contact their attorney to obtain advice with respect to any particular legal matter. No reader, user, or browser of this site should act or refrain from acting on the basis of information on this site without first seeking legal advice from counsel in the relevant jurisdiction. Only your individual attorney can provide assurances that the information contained herein – and your interpretation of it – is applicable or appropriate to your particular situation. Use of, and access to, this website or any of the links or resources contained within the site do not create an attorney-client relationship between the reader, user, or browser and website authors, contributors, contributing law firms, or committee members and their respective employers.
RFP Responses Examples: How to Respond to Common Requests
RFP Responses Examples: How to Respond to Common Requests
Handling discovery can be one of the most time-consuming parts of litigation. Each request for production (RFP) asks for specific documents that could affect the outcome of a case, so accuracy and organization are key.
Legal teams need a clear system for collecting, reviewing, and producing information while keeping everything compliant and easy to follow.
This guide breaks down what RFPs are, what makes a strong response, and includes real-world examples you can use for reference. In the final sections, we’ll look at how RFP automation tools can simplify the process and save time across multiple matters.
What Is a Request for Production?
A request for production is part of the discovery process in a lawsuit. It’s a formal written request that one party sends to another, asking for documents, records, or files that contain necessary information about the case.
These could include:
- Contracts
- Emails
- Reports
- Financial statements
- Any materials that help clarify the facts in dispute
The goal of an RFP is to make sure both sides have access to the same information before going to court. This makes sense because it allows each party to prepare its arguments based on complete and accurate evidence.
When a law firm receives an RFP, it reviews each request carefully, gathers the relevant materials, and decides which documents can be shared. Privileged or confidential data must be reviewed and redacted before being produced.
Managing this process manually takes time and increases the chance of missing important files. To handle it more efficiently, many firms use RFP automation tools that organize, tag, and produce documents automatically.
This saves hours of work and gives both the firm and the client confidence that every request has been handled correctly and consistently throughout the discovery process.
What Makes a Strong RFP Response
A strong RFP response depends on the case, the client, and the type of legal documents requested. But usually, here’s what makes an RFP response clear, defensible, and useful to both sides.
- Complete and accurate: It includes all the information requested, organized by request number and supported with clear references or exhibits.
- Concise and focused: The response avoids unnecessary detail and keeps the language direct. Each answer should make sense without long explanations.
- Well-structured: Every response lists the request first, followed by the reply. This helps readers follow the document easily.
- Relevant and precise: The response focuses only on materials related to the request and avoids mixing unrelated topics.
- Transparent: When documents are withheld or redacted, the reason is clearly stated. This helps demonstrate fairness in the discovery process.
- Professional tone: Even when objecting, the wording stays neutral and polite.
Sometimes, it’s also helpful to include additional information that clarifies how the data was collected or reviewed.
Overall, a good RFP response should demonstrate that the producing party handled the process carefully and in good faith. This shows both preparation and respect for the opposing side’s right to review evidence.
RFP Response Examples
These examples show how law firms usually structure their replies to different types of requests for production. They’re based on common discovery situations and demonstrate how to stay professional, clear, and compliant with court rules.
Each example reflects a different scenario:
Full Compliance Response
Request No. 1:
Produce all contracts signed between Plaintiff and Defendant from January 2021 through December 2023.
Response:
Defendant will produce all responsive documents. The legal team reviewed every contract within the requested time frame, confirmed that each document is accurate and complete, and attached the full set as Exhibit A.
No documents are being withheld. All materials were collected directly from the client’s files and verified before submission.
This example shows a thorough, direct reply written in active voice. It explains what actions the team took (reviewing, confirming, and attaching) and makes it clear that production is complete.
The language is confident, transparent, and easy to read, which helps maintain credibility during discovery.
Partial Compliance Response
Request No. 2:
Produce all internal emails between company executives regarding the product recall from 2020 to 2023.
Response:
Defendant objects to this request as overly broad and not limited in scope or time. After review, the legal team identified relevant communications concerning the Model X recall between March and August 2023.
Defendant will produce those emails as Exhibit B. All unrelated or privileged communications have been withheld.
This one shows how to comply in part while keeping the response reasonable. It demonstrates that the team reviewed the request, narrowed the focus, and provided only what was relevant.
Plus, the wording stays factual and professional, which acknowledges the discovery objection but still shows cooperation and good faith in the production process.
Objection Due to Scope or Relevance
Request No. 3:
Produce all employee performance evaluations from 2018 to 2024.
Response:
Defendant objects to this request on the grounds that it seeks irrelevant and confidential information not related to the issues in dispute. The request also lacks reasonable limits in time and subject matter. No documents will be produced in response.
This response shows a clear and professional objection. It explains the reason for refusing production (irrelevance and confidentiality) without unnecessary language. The response stays direct and avoids emotional or defensive wording.
A well-written objection like this helps protect client data while keeping the tone neutral and respectful, which can make future negotiations or revisions to the request smoother.
Clarification or Request for Narrower Terms
Request No. 4:
Produce all documents related to communications with third-party vendors.
Response:
Defendant objects to this request as vague and overly broad. It is unclear which vendors or time period the request covers.
Defendant requests clarification or a narrower scope limited to specific vendors and relevant projects. Once clarified, Defendant will review and produce responsive documents.
This type of response shows professionalism while maintaining control of the discovery process. It acknowledges the request, identifies the pain points, and invites clarification instead of rejecting the RFP issuer outright.
That approach demonstrates cooperation and helps avoid unnecessary disputes about scope or interpretation later in the case.
Extension or Need for Additional Time
Request No. 5:
Produce all reports and internal communications concerning the termination of the joint venture.
Response:
Defendant has begun collecting and reviewing the requested materials but requires additional time to complete the process. The legal team expects to finish review and production within 14 days.
Defendant will notify Plaintiff immediately once the responsive documents are ready for delivery.
This example reflects a practical and honest update. It shows that the responding party is taking action, managing the workload responsibly, and keeping communication open.
Formatting and Best Practices
A well-organized response makes the legal drafting process smoother and helps both sides review materials without confusion. Consistency across documents is key, especially when handling multiple RFPs in one case.
A clear format also reduces errors and gives the court more insight into how the documents were collected and reviewed.
Here are a few best practices for creating an effective RFP response:
- Use a clear structure: List each request, followed by its response. Keep numbering consistent throughout the entire process.
- Keep tone and language professional: Avoid unnecessary explanations or defensive language.
- Reference exhibits properly: Link each response to exhibits or attachments when relevant.
- Include an RFP cover letter: Summarize what’s being produced, note any objections, and provide contact details for follow-up.
- Work from a standard template: Templates save time, help maintain accuracy, and make future RFPs easier to manage.
Automation tools like AutoDoc make this far simpler. AutoDoc auto-drafts every RFP, cites exact Bates pages, and packages the finished response with its production, ready for review in seconds. In other words, it replaces weeks of manual review with one upload.
If you’d like to end repetitive discovery work, join the AutoDoc waitlist for early access and see how it can handle your next round of RFPs in just 3–10 seconds per request.
Automating RFP Responses
RFP response software helps legal teams create accurate responses to requests for production without spending hours on manual review.
It takes over the repetitive parts of the job, like collecting files, applying Bates numbers, formatting discovery responses, and organizing attachments. With those tasks out of the way, your team can focus on higher-level work.
If you’ve ever managed discovery manually, you know how time-consuming it can be to search through folders, rename files, and double-check references.
Automation replaces those steps with a structured system that identifies responsive documents, fills in response templates, and keeps everything consistent across cases.
Here’s what automated RFP tools often handle:
- Auto-draft responses: Build complete answers from uploaded files or data sources.
- Apply Bates numbers automatically: Assign clear page identifiers in seconds.
- Locate responsive materials: Detect and attach relevant files to each request.
- Support collaboration: Allow attorneys, paralegals, and other team members to review and edit in one shared workspace.
Automation lets your team spend less time on administrative work and more time supporting clients and refining case strategies.
It also keeps a reliable record of each action taken, so that every RFP response stays organized, consistent, and defensible throughout the discovery process.
End Repetitive RFP Work With Briefpoint Autodoc
Each RFP is different, but the goal stays the same: produce complete, accurate, and defensible responses without wasting days on formatting and document review. That’s where Briefpoint helps you work smarter.
With Briefpoint, you can propound and respond to RFPs, RFAs, and interrogatories across every U.S. state and federal district in just a few clicks.
Upload a discovery request, review AI-assisted objections, and export a formatted response ready to serve. It’s designed for real legal workflows that should be fast, defensible, and fully editable.
For teams managing heavy discovery workloads, Briefpoint eliminates the slow parts of the process. You’ll draft high-quality responses that match your firm’s preferred language, maintain compliance with local court rules, and keep every matter organized from start to finish.
Ready to see how it all works? Book a demo with Briefpoint today.
FAQs About RFP Responses Examples
What are examples of good RFP responses?
Good RFP responses are clear, complete, and well-organized. They address each request directly, include the right supporting documents, and explain any objections professionally. A strong response helps build trust with the opposing side by showing accuracy and transparency.
What are RFP responses?
RFP responses are written replies that a party provides during discovery to share or object to requested documents. They show which materials are being produced, which are withheld, and why.
What does a successful RFP look like?
A successful RFP response follows a clear plan, keeps formatting consistent, and references exhibits correctly. It’s also timely, defensible, and easy for others to review and understand.
How can you make RFP responses more engaging and complete?
Focus on clarity and relevance. Each response should maintain the reader’s interest, address the request with a direct solution, and present the information in a way that supports your overall case strategy.
The information provided on this website does not, and is not intended to, constitute legal advice; instead, all information, content, and materials available on this site are for general informational purposes only. Information on this website may not constitute the most up-to-date legal or other information.
This website contains links to other third-party websites. Such links are only for the convenience of the reader, user or browser. Readers of this website should contact their attorney to obtain advice with respect to any particular legal matter. No reader, user, or browser of this site should act or refrain from acting on the basis of information on this site without first seeking legal advice from counsel in the relevant jurisdiction. Only your individual attorney can provide assurances that the information contained herein – and your interpretation of it – is applicable or appropriate to your particular situation. Use of, and access to, this website or any of the links or resources contained within the site do not create an attorney-client relationship between the reader, user, or browser and website authors, contributors, contributing law firms, or committee members and their respective employers.
11 eDiscovery Best Practices for Defensible Discovery
11 eDiscovery Best Practices for Defensible Discovery
In modern litigation, electronic discovery has become a defining part of how cases are built and resolved. The growing volume of digital evidence means that every step, from identification to production, must be handled with care and consistency.
However, effective eDiscovery depends on more than technology. It’s about process, coordination, and documentation that keep teams aligned and data defensible.
While the best eDiscovery software can indeed make the work faster and more organized, strong results come from having a clear framework and disciplined execution behind every case.
So, in this guide, we’ll explore eDiscovery best practices that can help you manage data accurately, reduce risk, and stay prepared for every stage of discovery.
1. Define a Clear eDiscovery Strategy and Protocol
A clear eDiscovery strategy gives legal teams a structured approach throughout the entire process. It promotes consistency, reduces confusion, and keeps deadlines on track.
The plan should align with the Electronic Discovery Reference Model (EDRM), which outlines the following stages: identification, preservation, collection, processing, review, and production.
When creating your strategy, remember to:
- Set clear goals for scope, timelines, and team roles.
- Document every step to maintain transparency and defensibility.
- Use standard templates for data requests and productions.
- Define escalation points for handling disputes or technical issues.
- Update the plan regularly as laws, lawyer tools, and data sources change.
A written eDiscovery protocol forms the backbone of every matter. It should describe how data will be preserved, how privilege will be protected, and what file formats will be used for production.
This structure keeps everyone aligned from the start and helps prevent missing data or inconsistent handling later.
2. Involve Legal, IT, and Compliance Teams Early
Legal, IT, and compliance teams each play a unique role in managing electronically stored information (ESI), and early coordination prevents confusion later. When these teams work together from the start, identifying relevant data becomes faster and more accurate.
For example, when litigation is anticipated, the legal team defines the scope of discovery and which custodians may hold relevant ESI.
The IT department then identifies where that data lives (perhaps across cloud storage platforms, email servers, or internal systems) while compliance reviews the process to confirm it aligns with privacy and retention policies.
If these groups don’t align early, data could be lost, duplicated, or mishandled, putting the organization at risk of sanctions or missed deadlines.
Many organizations now rely on eDiscovery tools that let cross-functional teams collaborate in real time, centralizing case data and tracking progress from preservation to production.
A shared platform improves communication, reduces manual work, and keeps every department accountable.
For teams seeking a simpler, faster, and more reliable approach to document preparation during discovery, Briefpoint offers automation that turns complex requests into accurate, court-ready documents in minutes.
3. Identify and Preserve Data Sources Promptly
Quick identification and preservation of electronic data are key steps in the discovery process.
Once litigation is expected, legal teams must act fast to locate and secure relevant data before it’s altered or deleted. Delays can lead to spoliation or incomplete productions, both of which can harm a case.
The first step is mapping data sources, which means creating a clear record of where information is stored and who controls it. Common data sources include:
- Company email systems and archives
- Shared drives and document management tools
- Cloud storage platforms like Google Drive, OneDrive, or Dropbox
- Messaging apps such as Slack or Microsoft Teams
- Employee laptops, phones, or external devices
- Social media posts
Once these sources are identified, data collection should begin under defensible procedures that maintain metadata and prevent modification. Preservation notices must also be issued to custodians responsible for the data, suspending any auto-deletion or retention policies.
Plus, documenting each step of data preservation builds credibility and protects against challenges later in court. A consistent, repeatable approach keeps the process transparent and helps the team handle future matters more efficiently.
4. Use Legal Hold Procedures Effectively
A well-managed legal hold process is one of the most important parts of data preservation during discovery.
When a dispute or investigation is anticipated, legal professionals must suspend routine data deletion policies and preserve all potentially relevant ESI. This step prevents the loss of key evidence and demonstrates good faith compliance with the court.
A legal hold begins with a clear notice sent to custodians. Employees or departments likely to have relevant documents or electronic records. The notice explains what data must be preserved, how it should be handled, and who to contact with questions.
For instance, if a company expects litigation involving employment issues, HR staff and managers may receive a hold instructing them not to delete emails, reports, or internal chat messages tied to the event in question.
Tracking acknowledgments and sending reminders are equally important. Every action, from issuing the notice to releasing the hold, should be logged for transparency.
Many legal teams now use automated legal hold software to monitor compliance and record each step. This level of documentation protects the organization and confirms that data was preserved properly if the process is ever questioned in court.
5. Collect Data in a Defensible and Documented Way
Once a legal hold is in place and data preservation is confirmed, the next phase of the discovery process involves collecting that data for review. This transition is critical because any misstep during collection can damage file integrity or cast doubt on the evidence.
Moreover, data collection is one of the most sensitive parts of legal discovery, and every action must be defensible if challenged in court.
Legal teams should apply consistent procedures that maintain authenticity and retain relevant information exactly as it existed. This includes preserving metadata, timestamps, and detailed records of each activity.
Defensible collection often involves coordination between legal and IT teams. Data must be copied from secure data storage systems using approved forensic tools that prevent alteration.
For example, when collecting data from mobile devices, specialists may extract text messages or attachments in a controlled environment to preserve their original state.
A simple collection record may include:
- The person responsible for the collection and the date completed
- The tools or software used
- The source systems, such as email servers or cloud databases
Documenting every action supports strong information governance and demonstrates accountability. In large legal proceedings, complete records protect the organization from disputes about data handling and show that the collection followed a defensible process.
6. Leverage Advanced Search and Filtering Tools
Advanced search and filtering tools are core features of any modern eDiscovery platform. They allow legal teams to narrow large sets of data into smaller, more focused collections that matter to the case.
As data volumes continue to grow across emails, chat logs, and cloud solutions, these tools make it possible to manage the document review stage with precision and speed.
In the modern litigation process, the biggest eDiscovery challenges often involve identifying what’s relevant among thousands or even millions of files.
Keyword searches, date filters, and metadata queries help locate information quickly, while advanced analytics can detect duplicate files or similar content that might otherwise be reviewed multiple times.
Some systems also let users analyze log files or communication patterns to uncover hidden connections between custodians or data sources.
A strong review process combines these tools with attorney oversight to confirm accuracy and context. Automation alone can’t replace legal judgment, but it can remove the manual burden of sorting irrelevant material.
7. Apply Technology-Assisted Review or AI for Efficiency
Technology-assisted review (TAR) and AI-powered review systems have become standard in modern eDiscovery because they help manage the overwhelming amount of digital data generated in litigation.
Essentially, these technologies speed up the review of emails, documents, and messages while maintaining accuracy and consistency in how relevance and privilege are determined.
- Technology-assisted review: Uses machine learning and predictive coding to identify patterns in previously reviewed data, which allows the system to rank remaining documents by likelihood of relevance.
- Artificial intelligence: Expands on TAR by applying natural language processing and contextual analysis to understand meaning, not just keywords, across large datasets.
In practical terms, TAR and legal AI tools learn from attorney input and apply those lessons to new files, which helps teams prioritize what to review first. This reduces manual workload and accelerates the production of electronically stored information.
When used responsibly, TAR can cut review time by more than half and improve consistency in identifying data produced for disclosure. Combined with human oversight, these tools help legal teams meet discovery deadlines efficiently while keeping the process defensible.
8. Maintain Strong Chain-of-Custody Documentation
A clear chain of custody makes sure that every piece of evidence collected during eDiscovery can be trusted.
More specifically, it records how data moves from collection to review and production, showing that nothing was changed, lost, or mishandled. Strong documentation also supports regulatory compliance, especially in industries where audit trails are required.
To keep all teams on the same page, every handoff should be recorded in a chain-of-custody log. This log tracks:
- The names of key custodians involved in handling or accessing data
- The date and time of each transfer
- The storage location and transfer method used
- Verification notes confirming file integrity
For example, if an outside vendor receives a set of emails for review, the record should show when the transfer occurred, who approved it, and how the files were verified before upload. Each action must be timestamped and supported by documentation.
Maintaining this level of tracking not only protects against disputes but also helps in ensuring compliance with legal discovery standards. Courts expect transparency in how evidence is handled, and a reliable chain of custody provides exactly that.
9. Review and Redact Sensitive Information Carefully
During the review phase of eDiscovery, handling confidential data requires both precision and awareness of privacy laws and eDiscovery rules.
Legal teams must identify and redact sensitive content before further processing or production to avoid exposing personal or privileged material. Failure to do so can lead to sanctions, data breaches, or violations of legal requirements.
Examples of information that should be redacted include:
- Personal identifiers such as Social Security numbers or birth dates
- Financial details like bank account or credit card numbers
- Private communications covered by the attorney–client privilege
- Medical records or health-related data protected under HIPAA
One of the most common eDiscovery challenges is maintaining a balance between transparency and confidentiality. Automated redaction tools can speed up the process, but human review is still necessary to verify accuracy and context.
For instance, a legal AI system might flag names or numbers, but only an attorney can decide if they are relevant or privileged within the legal case.
Careful redaction protects both clients and opposing parties, keeping productions compliant and defensible. Every redaction decision should be logged and stored with a record of who approved it, so there is a clear audit trail for future reference.
10. Track Costs and Vendor Performance Throughout the Process
Monitoring expenses and vendor results is an often-overlooked part of the eDiscovery process, yet it has a direct impact on both budgets and case efficiency.
Each stage of discovery incurs measurable costs tied to storage, software licenses, and professional services. So, keeping a detailed record of these figures helps legal teams forecast spending, justify budgets, and identify where savings are possible in future matters.
For example, a law firm working with multiple vendors might notice that one provider charges significantly higher rates for hosting data but delivers slower turnaround times.
Tracking this performance over several projects makes it easier to decide who offers the best value. Metrics like average processing time, accuracy rates, and responsiveness can help build a clear picture of which partnerships are most effective.
Many firms now use dashboards or litigation management software to centralize cost data, automate invoices, and monitor key metrics in real time.
In other words, treating cost and performance tracking as part of the standard workflow keeps the overall eDiscovery process both predictable and efficient.
11. Regularly Update and Refine eDiscovery Policies and Technology
Finally, every organization should treat its eDiscovery policies as living documents that evolve with new data sources, laws, and legal tech software.
Some areas that should always be reviewed include:
- Backup tapes: Make sure retention schedules reflect current storage limits and recovery options.
- Preservation measures: Reassess how data is secured to avoid accidental loss or overwriting.
- Collecting ESI: Verify that approved tools and methods maintain file integrity and defensibility.
- Producing electronically stored information: Confirm that file formats and transfer protocols meet court and client expectations.
Keeping eDiscovery tools and practices updated not only supports compliance but also reduces manual work. Teams that modernize their approach are better equipped to manage complex matters efficiently.
Autodoc, the newest solution from Briefpoint, takes this a step further. It ends manual discovery work by turning productions and case files into ready-to-serve discovery responses (with Bates numbering and page-level citations) in just seconds.
Book a demo and be among the first to automate their discovery responses.
Briefpoint and the Future of eDiscovery
Strong eDiscovery practices are built through structure, collaboration, and the right technology to keep everything moving smoothly. Each stage of discovery, from locating data to preparing final productions, depends on accuracy and clear communication.

And when teams work within a defined system, discovery becomes less chaotic and more predictable.
Briefpoint helps make that happen. It replaces repetitive manual work with automation that drafts, numbers, and formats discovery responses in just minutes. The result is more time for strategy, stronger client outcomes, and less effort spent on administrative tasks.
If you’re ready to simplify discovery and see what faster, smarter document preparation looks like, book a Briefpoint demo today.
FAQs About eDiscovery Best Practices
What is the identification phase in eDiscovery?
The identification phase is the first step in locating potentially relevant data for a case. It involves data mapping, identifying custodians, and determining which systems or devices hold important files. This stage helps create a clear plan for collecting and reviewing information later in the process.
How should law firms handle data from personal devices?
When employees use personal devices for work-related matters, those devices may contain relevant electronic communication, such as emails or text messages. Legal teams must balance privacy concerns with discovery obligations by following clear policies and using defensible collection methods approved by regulatory bodies or the court.
What is the standard retention period for eDiscovery materials?
A standard retention period varies depending on jurisdiction and industry. Most organizations align their retention schedules with local laws or third-party subpoena requirements. It’s best practice to consult internal legal support teams to confirm how long records should be maintained.
Why is production format important in eDiscovery?
Choosing the right production format affects how the opposing party can review and analyze data. Courts often request files in native format, digital form, or electronic format with proper metadata and load files to maintain data integrity and preserve context.
How can firms protect attorney-client communications during discovery?
Firms protect attorney-client communications by marking privileged materials, using privilege logs, and reviewing every document before responding to discovery requests or attempting to obtain discovery. Careful review prevents accidental disclosure and keeps the privilege intact throughout the process.
The information provided on this website does not, and is not intended to, constitute legal advice; instead, all information, content, and materials available on this site are for general informational purposes only. Information on this website may not constitute the most up-to-date legal or other information.
This website contains links to other third-party websites. Such links are only for the convenience of the reader, user or browser. Readers of this website should contact their attorney to obtain advice with respect to any particular legal matter. No reader, user, or browser of this site should act or refrain from acting on the basis of information on this site without first seeking legal advice from counsel in the relevant jurisdiction. Only your individual attorney can provide assurances that the information contained herein – and your interpretation of it – is applicable or appropriate to your particular situation. Use of, and access to, this website or any of the links or resources contained within the site do not create an attorney-client relationship between the reader, user, or browser and website authors, contributors, contributing law firms, or committee members and their respective employers.